What is AES-GCM?
AES-GCM stands for Advanced Encryption Standard-– Galois Counter Mode. It is used in various applications that require secure communication and data authentication. While GCM is the mode of operation, AES is the encryption standard. Together, AES-GCM makes a symmetric cryptography algorithm used in various cryptography protocols. AES-GCM provides both authenticated encryption (confidentiality and authentication) and the ability to check the integrity and authentication of additional authenticated data (AAD) that is not encrypted. AES-GCM is one of the recommended block cipher modes of operation, per NIST Special Publication 800-38D [1].
The mode is widely used in practice and is part of many standards.

AES-GCM implementation is complex ([2]). Since AES architecture uses a lookup table (S-Box) indexed by secret data, one must use some side-channel attacks resistant techniques to achieve both performance and security.
Below, you can find a high-level flow diagram of the AES-GCM algorithm (more details about implementation can be found in [2][3]):
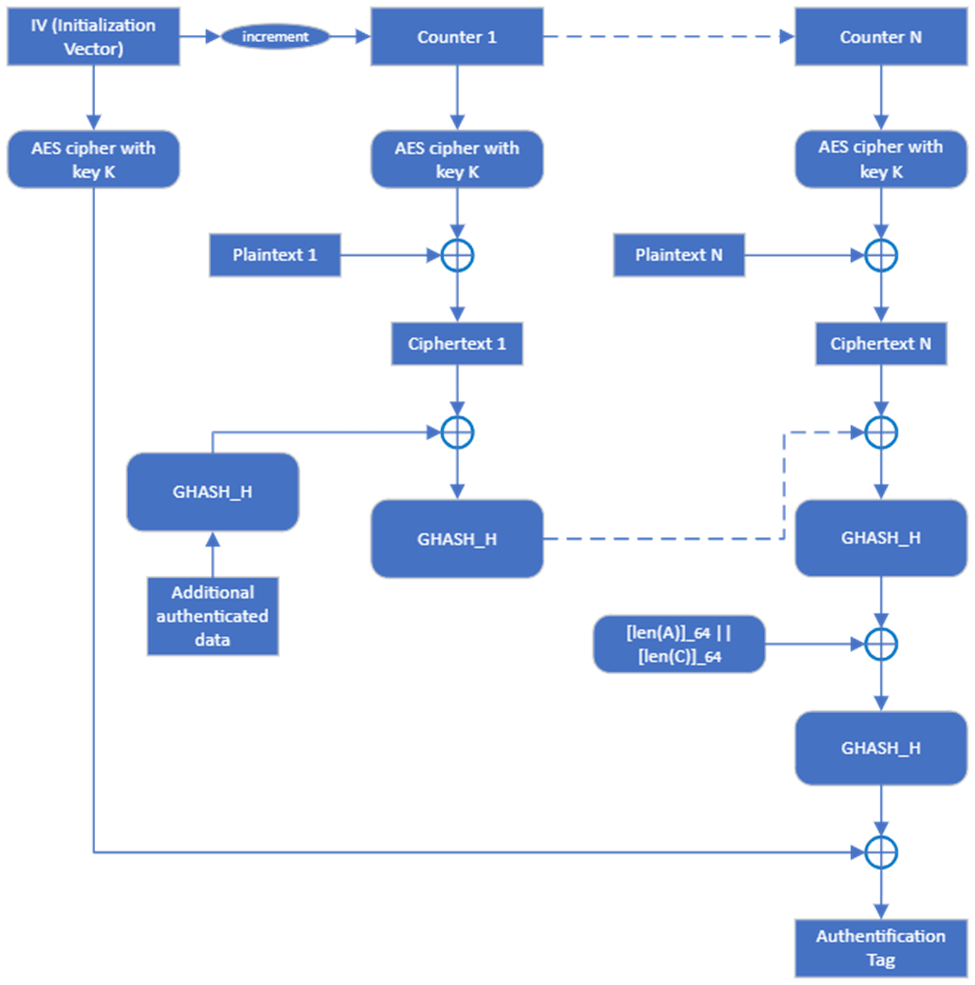
Figure 1. AES-GCM authenticated encryption diagram.
AES-GCM Support in Intel® IPP Cryptography and OpenSSL Libraries
Due to the complexity of the AES-GCM algorithm, it is more convenient to use it as out of the box implementation from the software libraries instead of implementing it yourself.
As good examples of performant and highly functional verification tested implementations of this algorithm, you can refer to the following libraries:
- OpenSSL - a robust, commercial-grade, full-featured toolkit for general-purpose cryptography and secure communication. [4]
- Intel® Integrated Performance Primitives Cryptography (Intel® IPP Cryptography) - a secure, fast, and lightweight library of building blocks for cryptography, highly optimized for various Intel® CPUs. [5]
Below is an example demonstrating how to use the AES-GCM algorithm in OpenSSL [6] and Intel IPP Cryptography.
OpenSSL and Intel IPP Cryptography AES-GCM Code Example
| OpenSSL Example | Intel IPP Cryptography Example |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
As we can see, OpenSSL and Intel IPP Cryptography API are easy to use with clear calling conventions. Using 3rd party libraries allows the users not to spend extra time and resources on AES-GCM implementation, optimization, and testing. Instead, they can complete their software using ready-to-use algorithms as part of an out-of-the-box solution.
AES-GCM Performance
Intel IPP Cryptography contains implementations of the AES-GCM algorithm that are highly optimized for Intel CPUs by utilizing
- Intel® AES New Instructions (Intel® AES-NI)
- Intel® Vector Extension for AES-NI
- Intel® PCLMULQDQ
- Intel® Vector Extension for PCLMULQDQ
Below, you can see the performance comparison between OpenSSL and IPP Cryptography for the message size 16384 bits on 4th Generation Intel Xeon Scalable Processors.
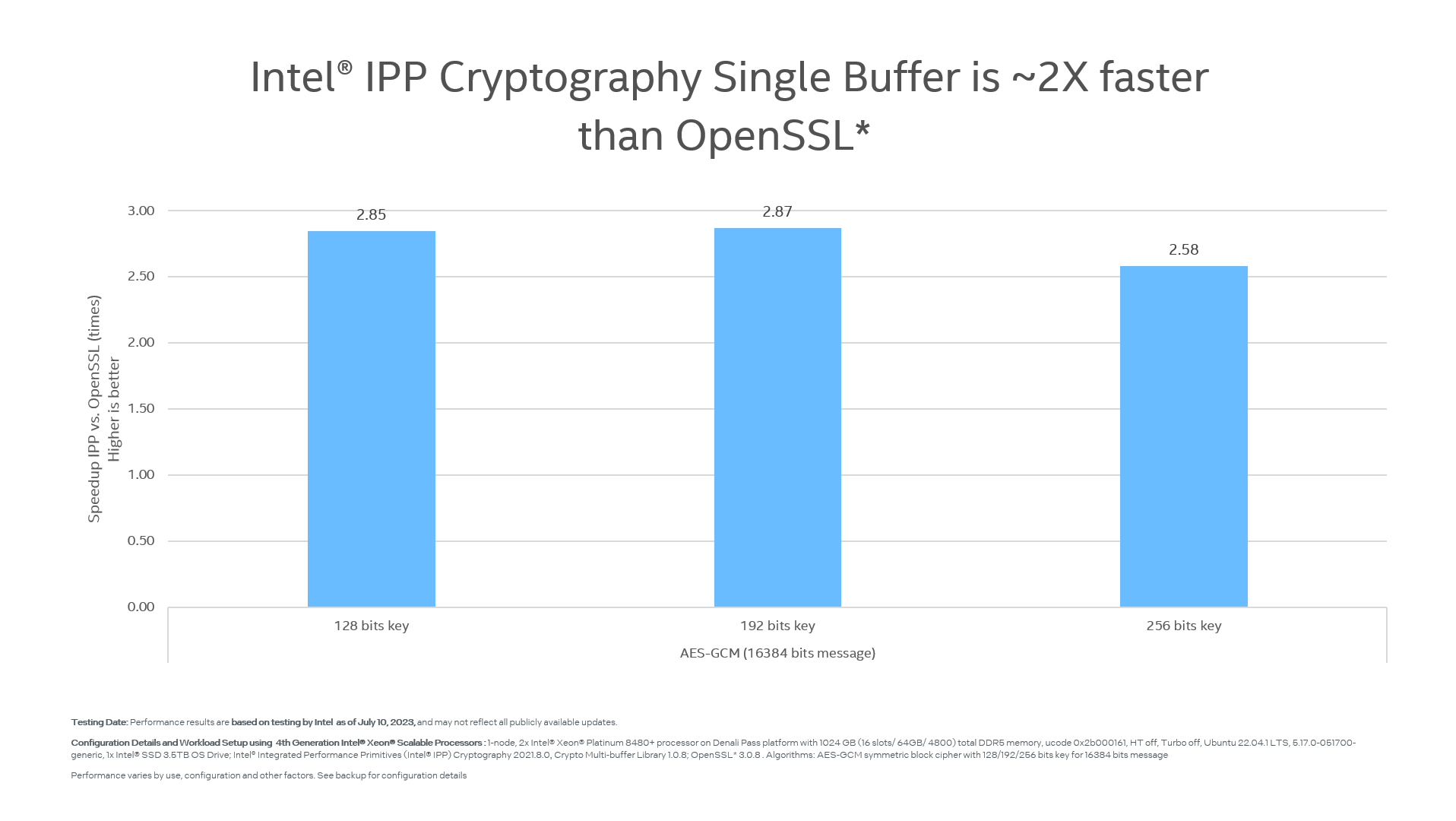
Figure 2. OpenSSL vs. Intel IPP Cryptography performance comparison for AES-GCM algorithm
Intel IPP Cryptography continues to work on additional optimizations of the cryptography algorithms. The recently released Intel IPP Cryptography 2021.9 version contains additional optimizations based on Intel® Advanced Vector Extensions 2 (Intel® AVX2) and Intel® Vector Extension for AES-NI and PCLMULQDQ.
The chart below demonstrates AES-GCM performance speed-up between two Intel IPP Cryptography releases:
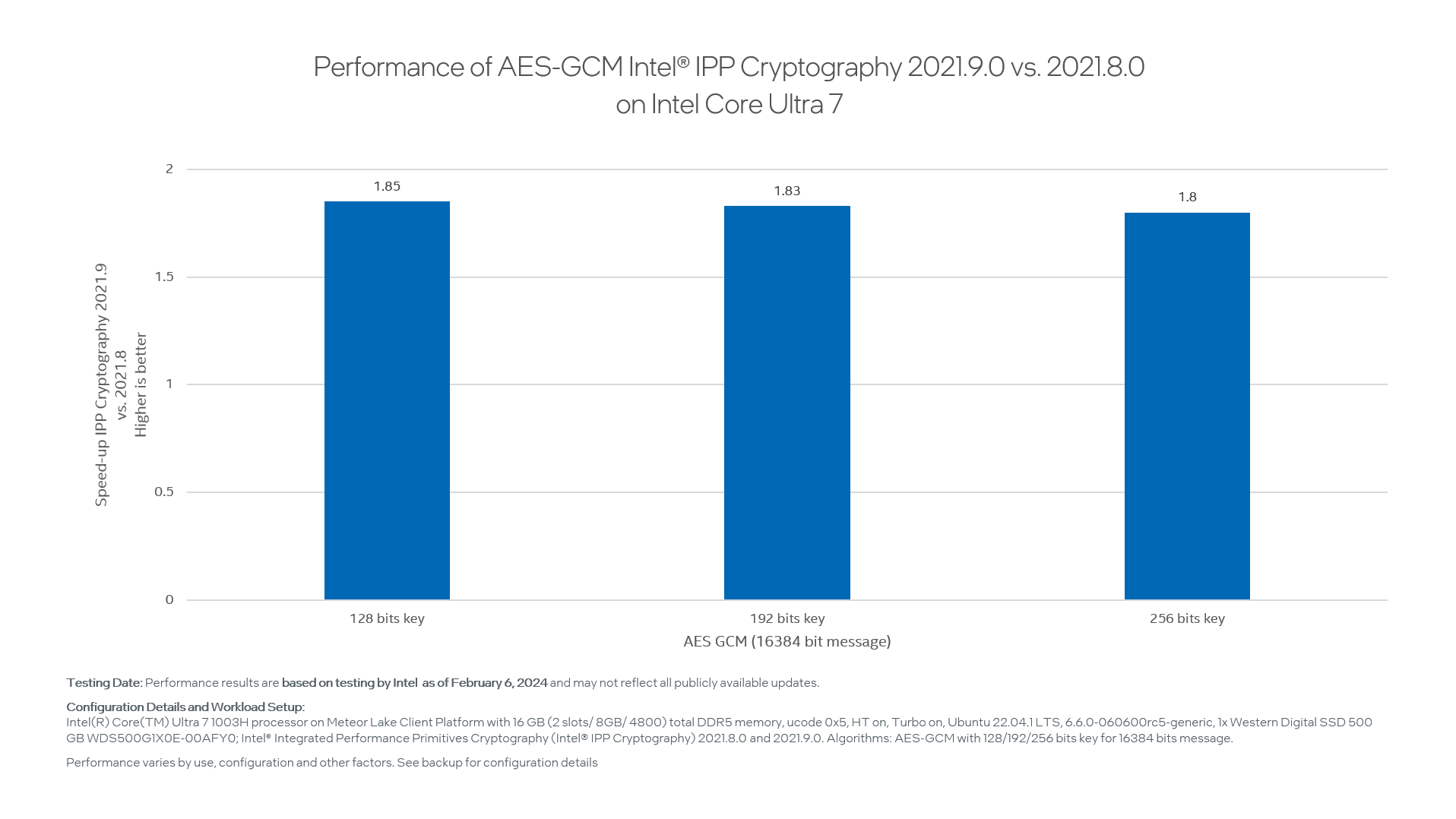
Figure 3. Performance comparison between Intel IPP Cryptography 2021.9 and 2021.8 releases
Summary
AES-GCM is one of the most common symmetric cipher algorithms used in a variety of different spheres of the modern world. Intel IPP Cryptography brings differentiative performance on Intel CPU. The complexity of the algorithm makes it resilient against different attacks. This complexity, however, can also make its implementation challenging. Developers look for ease of use, fast implementation, and highly optimized execution speed. Performance is critical for many applications. Therefore, OpenSSL, Intel IPP Cryptography, and other libraries implement and optimize the algorithm for the latest available hardware.
Get the Software
You can install the Intel® Integrated Performance Primitives Cryptography (Intel IPP Cryptography) as a part of the Intel® oneAPI Base Toolkit. You can also download a stand-alone version of the library or test it across Intel® CPUs and GPUs on the Intel® Developer Cloud platform.
References
[1] Planning Note for Revision (2023), NIST Recommendation for Block Cipher Modes of Operation: Galois/Counter Mode (GCM) and GMAC
[2] Morris Dworkin (2007), NIST Recommendation for Block Cipher Modes of Operation: Galois/Counter Mode (GCM) and GMAC, NIST Special Publication 800-38D
[3] David A. McGrew, John Viega (2005), The Galois/Counter Mode of Operation (GCM)
Additional Resources
[4] OpenSSL GitHub
[5] Intel IPP Cryptography GitHub
[7] Intel IPP Cryptography AES-GCM Documentation
[8] Advanced Encryption Standard Galois Counter Mode – Optimized GHASH Function Technology Guide